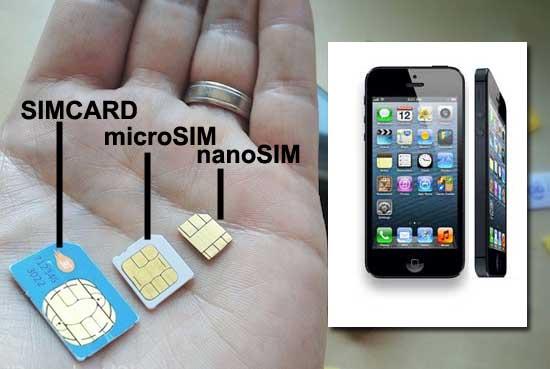
The smaller SIM standard goes even more smaller as Apple trims the iPhone’s thickness by 18%.
Your existing normal SIM or Micro SIM can be converted to Nano SIM by following simple steps. To do this, you have two options: DIY or visit your wireless network’s local customer service center and get them to replace your current SIM with a Nano SIM. But we know if you came to this DIY guide, your intent is to Do It Yourself, lets get started
What you need:
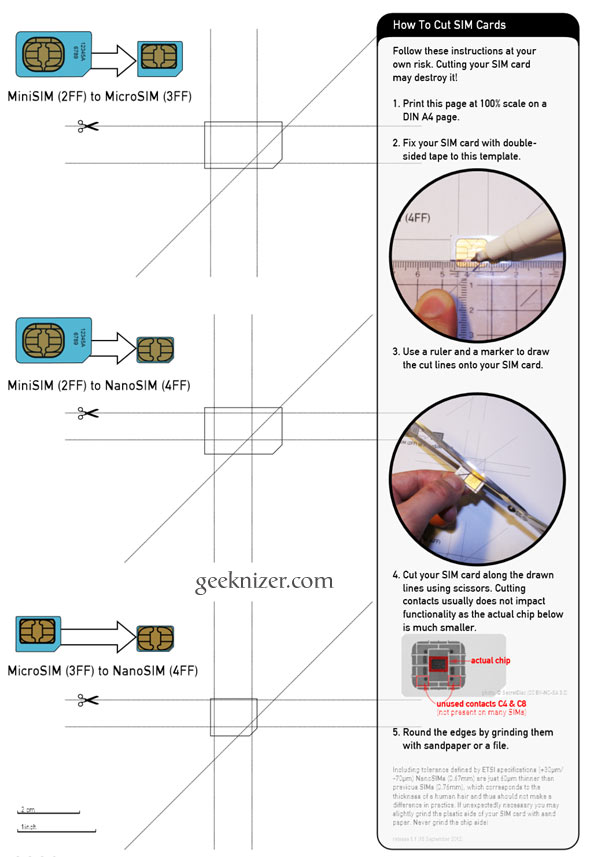
Step 2: Accurately place your current SIM card on the designated area. If you have a Mini SIM, place it on the second highlighted area. If you have Micro SIM, place it on the third and last. When you’re sure it matches the outlines, stick the SIM to paper using a tape.
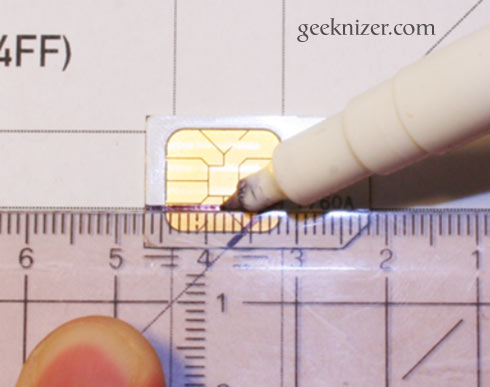
Step 3: Using a ruler and a marke, carefully mark the five lines along which you would cut in the following step.
Bingo, you have successfully made Nano SIM for your iPhone 5.
Apple has really left no plastic area on the SIM card. Its hard to say what they would have in the iPhone 6. Perhaps a pico-SIM or femto-SIM card.
Your existing normal SIM or Micro SIM can be converted to Nano SIM by following simple steps. To do this, you have two options: DIY or visit your wireless network’s local customer service center and get them to replace your current SIM with a Nano SIM. But we know if you came to this DIY guide, your intent is to Do It Yourself, lets get started
What you need:
- A printer (Colored or monochrome)
- A4-sized sheet
- Tape
- Ruler and marker
- Good Scissors
- Sandpaper or file
- Patience & accuracy
How to Make Nano SIM card for iPhone 5
Step 1: Download & print PDF at 100% scale on an A4 page.Step 2: Accurately place your current SIM card on the designated area. If you have a Mini SIM, place it on the second highlighted area. If you have Micro SIM, place it on the third and last. When you’re sure it matches the outlines, stick the SIM to paper using a tape.
Step 3: Using a ruler and a marke, carefully mark the five lines along which you would cut in the following step.
Step 4: Use the scissor to carefully cut across the
marked lines. You really need to be slow and
accurate. Single mistake
can damage your SIM card. Ask your mom if you’ve to, she might be able to do it better.
Step 5: Using a file or sand paper, Smooth out the edges of your Nano SIM.Bingo, you have successfully made Nano SIM for your iPhone 5.
Apple has really left no plastic area on the SIM card. Its hard to say what they would have in the iPhone 6. Perhaps a pico-SIM or femto-SIM card.